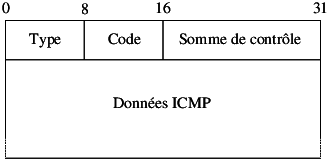
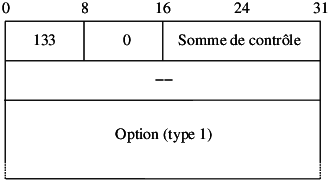
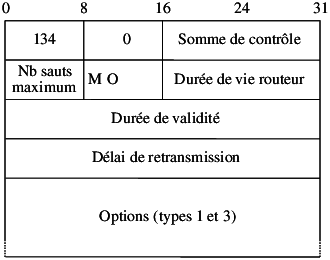
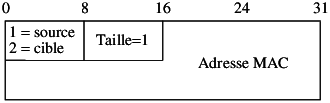
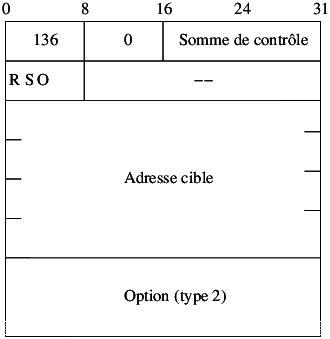
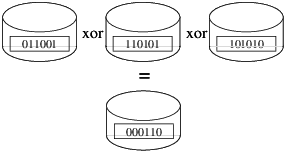
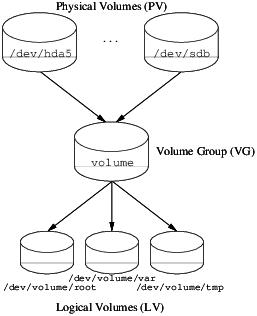
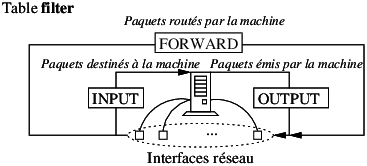
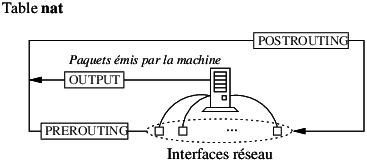
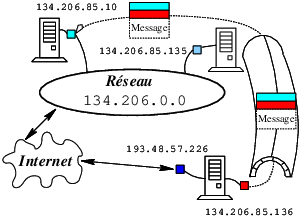
Definition de SE virtuel (e.g. /etc/xen/fourmies.cfg) :
kernel = '/boot/vmlinuz-2.6.32-5-xen-686'
ramdisk = '/boot/initrd.img-2.6.32-5-xen-686'
memory = '1024'
root = '/dev/xvda1 ro'
disk = [
'file:/usr/local1/xen/domains/fourmies/fourmies_root.img,xvda1,w',
'file:/usr/local1/xen/domains/fourmies/fourmies_swap.img,xvda2,w',
'file:/usr/local1/xen/domains/fourmies/fourmies_tmp.img,xvda5,w',
'file:/usr/local1/xen/domains/fourmies/fourmies_var.img,xvda6,w',
'file:/usr/local1/xen/domains/fourmies/fourmies_home.img,xvda7,w',
'file:/usr/local1/xen/domains/fourmies/fourmies_log.img,xvda8,w',
'phy:/dev/spool1/mail-spool,xvdb1,w',
'phy:/dev/spool2/mail-backup,xvdc1,w'
]
name = 'fourmies'
dhcp = 'dhcp'
vif = [ 'mac=00:16:3E:52:80:93, bridge=bridge2' ]
on_poweroff = 'destroy'
on_reboot = 'restart'
on_crash = 'restart'